Blog
Enjoy our latest posts and create posts that educate and inform
Digital Transformation as a Strategic Business Imperative
Digital transformation is often misunderstood as the simple adoption of new technologies or tools. True transformation goes beyond technology adoption, it involves redefining how […]
Read MoreEmerging Technologies – Foundation For Sustainable Competitive Advantage
Emerging technologies are redefining competitive advantage across every sector. However, technology alone does not create differentiation—execution does. Organizations that understand […]
Read MoreArtificial Intelligence as a Career
Artificial Intelligence is no longer just a buzzword or a tool reserved for tech specialists. It has become a core […]
Read MoreWhat is Passwordless Authentication?
Passwordless authentication is an authentication method that allows a user to gain access to an application or IT system without […]
Read MoreMFA Fatigue Attacks: How to Safeguard Your Data and Network
Cybersecurity is a never-ending battle, with network protection and data security at its core. In an era marked by digital […]
Read MoreStrategic BYOD Management: The ‘Why’ and ‘How’ for Businesses
The workplace is evolving at a rapid pace, and one of the notable changes is the proliferation of Bring Your […]
Read MoreDoes AI Disruptions Pose Threats to the Traditional Workplace
Artificial Intelligence (AI) stands at the crossroads of transformation and disruption for the traditional workspace. This technology has the potential […]
Read MoreDigital Trust: Technology as a Service
Technological solutionism — the idea that tech developers can be trusted to innovate or code our way out of problems, […]
Read MoreThe Utilization of Emerging Technologies as a Service
The utilization of emerging technologies a service provides a competitive advantage to XaaS (Anything as a Service) adopters who leverage […]
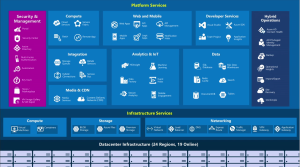
Read MoreHow to Build IoT Solutions Using Microsoft Azure IoT
Building IoT solutions using Microsoft Azure IoT can seem like a complex task, but with the right guidance, it becomes […]
Read MoreIntroduction to Azure IoT
The Internet of Things (IoT) industry has continued to expand and permeate people’s daily lives over the past few years. […]
Read MoreIntroduction to Azure IoT Edge
Microsoft Azure IoT Edge is the technology from Microsoft for building Internet of Things (IoT) solutions that utilize Edge Compute. […]
Read More